Data race through standard library function call
Multiple tasks make unprotected calls to thread-unsafe standard library function
Description
This checker is deactivated in a default Polyspace® as You Code analysis. See Checkers Deactivated in Polyspace as You Code Analysis (Polyspace Access).
This defect occurs when:
Multiple tasks call the same standard library function.
For instance, multiple tasks call the
strerrorfunction.The calls are not protected using a common protection.
For instance, the calls are not protected by the same critical section.
Functions flagged by this defect are not guaranteed to be reentrant. A function is reentrant if it can be interrupted and safely called again before its previous invocation completes execution. If a function is not reentrant, multiple tasks calling the function without protection can cause concurrency issues. For the list of functions that are flagged, see CON33-C: Avoid race conditions when using library functions.
To find this defect, you must specify the multitasking options before analysis. To specify these options, on the Configuration pane, select Multitasking. For more information, see Configuring Polyspace Multitasking Analysis Manually.
Risk
The functions flagged by this defect are nonreentrant because their implementations can use global or static variables. When multiple tasks call the function without protection, the function call from one task can interfere with the call from another task. The two invocations of the function can concurrently access the global or static variables and cause unpredictable results.
The calls can also cause more serious security vulnerabilities, such as abnormal termination, denial-of-service attack, and data integrity violations.
Fix
To fix this defect, do one of the following:
Use a reentrant version of the standard library function if it exists.
For instance, instead of
strerror(), usestrerror_r()orstrerror_s(). For alternatives to functions flagged by this defect, see the documentation for CON33-C.Protect the function calls using common critical sections or temporal exclusion.
See
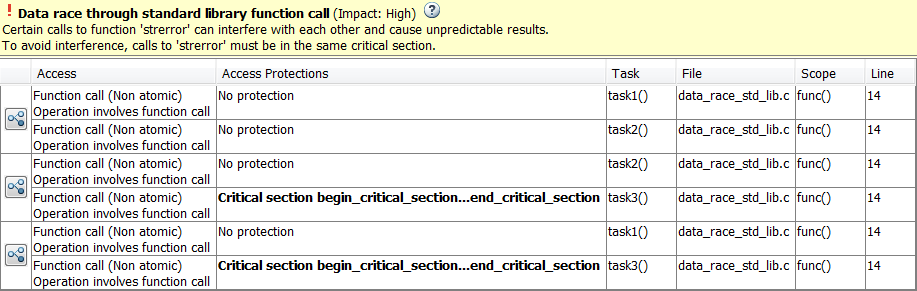
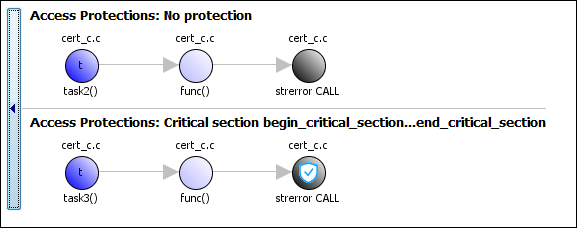
Critical section details (-critical-section-begin -critical-section-end)andTemporally exclusive tasks (-temporal-exclusions-file).To identify existing protections that you can reuse, see the table and graphs associated with the result. The table shows each pair of conflicting calls. The Access Protections column shows existing protections on the calls. To see the function call sequence leading to the conflicts, click the
 icon. For an example, see below.
icon. For an example, see below.
Examples
Result Information
| Group: Concurrency |
| Language: C | C++ |
| Default: On |
Command-Line Syntax: DATA_RACE_STD_LIB |
| Impact: High |
Version History
Introduced in R2016b
See Also
Temporally exclusive tasks (-temporal-exclusions-file) | Critical section details (-critical-section-begin -critical-section-end) | Tasks (-entry-points) | Configure multitasking manually | Find defects (-checkers) | Data race | Destruction of locked mutex | Double lock | Double unlock | Missing lock | Missing unlock
Topics
- Analyze Multitasking Programs in Polyspace
- Protections for Shared Variables in Multitasking Code
- Interpret Bug Finder Results in Polyspace Desktop User Interface
- Interpret Bug Finder Results in Polyspace Access Web Interface (Polyspace Access)
- Address Results in Polyspace User Interface Through Bug Fixes or Justifications
- Address Results in Polyspace Access Through Bug Fixes or Justifications (Polyspace Access)